This article will go through how to use free encryption software. Even the most daring Sci-Fi authors of the past could never have predicted how connected our modern world is. The Internet, of course, is the medium via which this interconnection is achieved. And, on the Internet, everything is built on the data that human users provide– even if they don’t acknowledge it. Yes, we recommend you in particular.
Best Free Encryption Software
Here are some details about free encryption software that you may learn about in this article: Your personal or professional information is out there, and unless you take action, it may always fall into the wrong hands. Finding a solution, of course, entails putting matters into your own hands and beginning to secure all of the information you do not want to be made public. In this article, we’ll show you how to use the best free encryption software available today so you can take control of your data and security.
14 Best Free Encryption Software In 2022
We have compiled a list of the best encryption software of 2022, Let’s have a look at the list given below.
1. BitLocker
Windows BitLocker is one of the most widely used regional data encryption solutions. It is preferred by a large number of users. It allows you to encrypt a single partition on your hard drive or the entire hard disc drive. BitLocker is a built-in feature of recent Windows versions (starting with Windows 10), and it encrypts partitions using AES 128 and 256 bits. (AES) is the industry standard for encryption algorithms, and it’s used by every VPN worth its salt, every military institution on the planet, and the vast majority of governmental organizations.
WEBSITE URL: https://docs.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-overview
2. VeraCrypt
VeraCrypt is a free encryption program available for Windows, macOS, and, most importantly, Linux. Like BitLocker, the software supports AES. However, it also includes two more effective encryption algorithms (TwoFish and Snake) that you can use in conjunction with AES to create up to three encryption levels on a single volume– the ideal tool for those of us who prefer to go overboard. VeraCrypt is a free and open-source alternative to Truecrypt. That’s because it inherited the goal of TrueCrypt, a previous project from around the same period that was abandoned by the development team.
WEBSITE URL: https://www.veracrypt.fr/code/VeraCrypt/
3. NordVPN
Many people consider (VPN) to be the ultimate Internet security solution. Unfortunately, this isn’t always the case. VPNs are tools, and like any other tool, they can be utilized effectively or incorrectly to achieve or defeat a goal. If a VPN correctly performs two tasks: masking your IP address and protecting your traffic, it will improve your security and privacy. Yes, Tor does this, but keep in mind that it only applies to the Tor browser. A VPN provides you with those two services for all of the traffic that comes in and out of your device. Personal privacy, on the other hand, is another matter. Everything you do on the internet using a virtual private network (VPN) is routed through the VPN’s servers. As a result, your supplier is aware of everything you’re doing.
WEBSITE URL: https://nordvpn.com/
4. BCArchive
BCArchive is a freeware Windows folder encryption program. For a Windows program, it provides a surprising amount of flexibility. It allows you to encrypt a full folder or a single file, depending on your preference, using a number of the best encryption algorithms available. Blowfish-448, Blowfish-256, Twofish, Gost, Rijndael, Snake, and Camellia-256 are among the algorithms in this list, which is even better than VeraCrypt. We also get a number of hash methods to finish for various tasks, as well as a public key encryption approach.
WEBSITE URL: https://bcarchive.en.softonic.com/
5. PixelCryptor
PixelCryptor is a folder encryption program that is available for free. So, what operating system does it use? You guessed it! It’s a Windows program! PixelCryptor’s encryption technology has a unique approach in the business. It makes use of the pixels from a bitmap file. So you choose a picture to encrypt, and the image’s file becomes both an encryption secret and a password. Decrypting the files necessitates the recipient having access to the exact identical file. Replacing a password and/or encryption key for a file eliminates the hassle of creating a secure password, remembering it, securely communicating it to the other person, and so on. As a result, it’s appealing in a variety of ways.
WEBSITE URL: https://pixelcryptor.en.softonic.com/
6. LastPass
LastPass is one of the most well-known password managers on the planet. Unfortunately, the functionalities are limited in the free version, but it may still safeguard your passwords and personal information. Furthermore, this piece of software will allow you to get rid of that physical notebook where you’ve been saving all your passwords up until now (or any other similar resource you’ve used up until now, which is normally unsafe). The user interface is simple, intuitive, and simple to use. In addition, the technology platform comprises Mozilla Firefox and Google Chrome browser extensions, as well as Android and iOS mobile apps.
WEBSITE URL: https://www.lastpass.com/
7. FileVault 2
So you’re a happy Mac user looking for an encryption solution that’s tailored to Apple’s distinct preferences? Look no further. FileVault 2 is exactly what you’re looking for. This app encrypts your Mac’s whole hard drive with AES-128 encryption and a 256-bit key. We understand your skepticism: why isn’t AES-256 used instead? Why do Mac users only get half the power that everyone else does? AES-256 has been approved as being more powerful than the 128-bit version of the same algorithm. However, don’t underestimate the significance of (AES-128). So far, it’s passed every audit, and no known attack has been able to breach it– which isn’t for a lack of trying.
WEBSITE URL: https://www.techrepublic.com/article/apples-filevault-2-encryption-program-a-cheat-sheet/
8. DiskCryptor
DiskCryptor can encrypt your external and internal hard discs, as well as system partitions and ISO images, USB thumb drives, and other storage media. It’s an open-source Windows task that, like VeraCrypt, supports Twofish and Snake in addition to AES. It’s simple, intuitive, and effective, allowing you to encrypt a full hard disc by simply selecting it and pressing “Encrypt.”
WEBSITE URL: https://diskcryptor.org/
9. 7-Zip
Encrypting an entire partition or a whole disc isn’t for everyone. Many users, on the other hand, are aware of which submissions require the extra protection provided by encryption, and they prefer a tool that can perform that duty. Activate 7-Zip. This is yet another free and open-source task that is well-known for its ease of use, speed, and convenience. It’s based on AES-256 encryption, and if you’ve used WinZip or WinRar before, you’ll find it extremely comfortable right now. For the most part, it accomplishes the same goal, but with the added benefit of high-level encryption.
WEBSITE URL: https://www.7-zip.org/
10. AxCrypt
AxCrypt is similar to 7-Zip in that it is also free open-source software that encrypts individual files in a similar fashion. Premium versions for Windows, iOS, Android, and macOS are readily available. With a simple right-click, the user interface can apply AES-256 to a single file, folder, or group of files. You can either encrypt your files for a set period of time or have the program decode them as soon as they arrive at their destination.
WEBSITE URL: https://axcrypt.net/
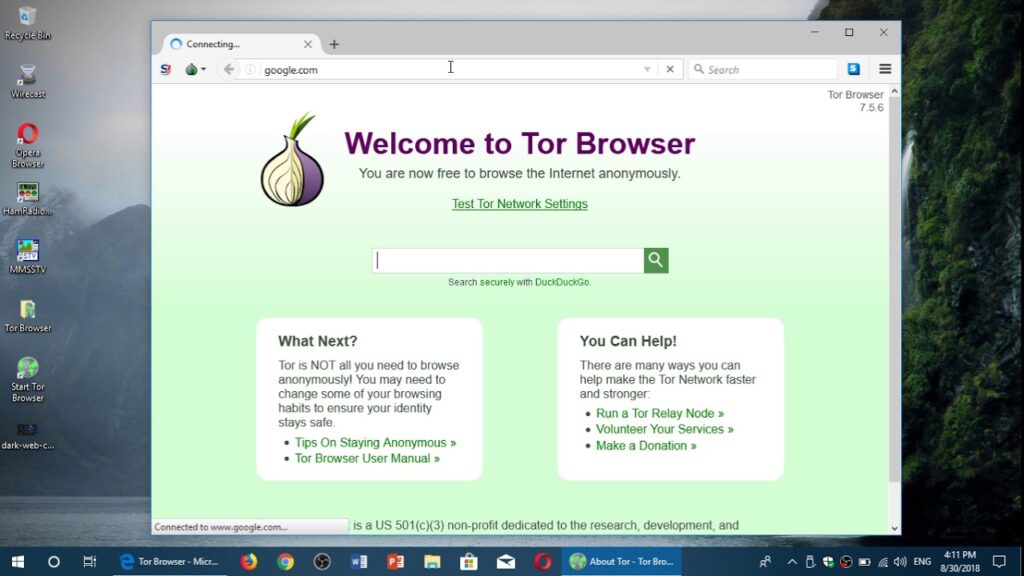
11. Tor Web browser
The Tor web browser is one of the few tools that effectively guarantees personal privacy, anonymity, and security online. It allows you private access to the internet and encrypts all of your data. It also masks your IP address by preventing several common plugins (Flash, RealPlayer, Quicktime) from revealing it. The Tor Browser is a customized version of Mozilla Firefox that connects to the Tor network. The network provides IP masking and encryption, ensuring that the prey website you visit has no idea where you are and that no third parties can learn about your activities.
WEBSITE URL: https://play.google.com/store/apps/details?id=org.torproject.torbrowser&hl=en&gl=US
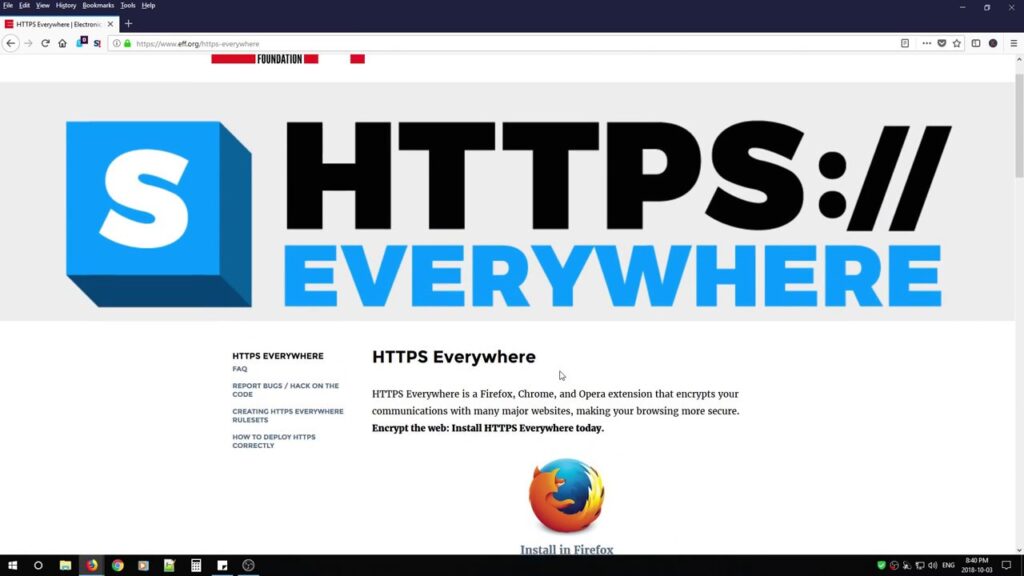
12. HTTPS Everywhere
Securing your regional files or partitions is unquestionably a good security policy. However, it is insufficient. Because communication is at the heart of the Internet, you must be certain that your communications do not give your game away to cybercriminals. In this example, we’re discussing the most prevalent and important internet activity: web browsing. There are insecure and secure ways to browse the internet, and you must always choose the safe option. That’s what it’s capable of doing for you.
WEBSITE URL: https://chrome.google.com/webstore/detail/https-everywhere/gcbommkclmclpchllfjekcdonpmejbdp?hl=en
13. Silver Secret
Silver Key is a free encryption program for Windows. This one’s goal is to create an encrypted package that you can send over the Internet without fear of being intercepted. If you provide the correct password for a provided package, it can even self-extract. As a result, the user does not need to have Silver Key installed in order to decrypt the information you provide them. The algorithm for cryptography is (AES 256). It is a market requirement for cryptography, VPNs, and any job that requires the highest level of encryption.
WEBSITE URL:
14. Sophos Free Encryption
This time, it’s a Windows folder encryptor. This one gives you the option to compress your folder, saving space on your storage devices and speeding up the data transfer process. Sophos Free Encryption also allows you to generate a self-extracting encrypted archive (similar to Silver Secret), which improves the effectiveness of encrypted shipments by eliminating the need for the recipient to download additional software to view the “plain text” contents.
WEBSITE URL: https://ccm.net/downloads/security-and-maintenance/6599-sophos-free-encryption/
Conclusion
It is not a luxury to be safe online. It’s a requirement. In the human experience, the digital way of living is a brand-new function. In the last few years, it’s grown tremendously. As a result, most of us have no idea how to cope with it correctly because our grandparents could not have taught us anything. But, no matter how new this thing is, or how simple it may be for anyone who is uneducated in it to understand it, the fact remains that if our identity is stolen online, our important working data is erased or corrupted, or our personal information is shared outside, we will find ourselves in a world of problems and pain.