In the modern day, organizations are more connected than ever. Private networks, systems, and equipment are a requirement for any effective organization or firm. Firewalls are a key line of defense for defending these networks against malicious attacks. Whether they are traditional firewalls or “next-generation” technologies, firewalls are a fundamental component of an organization’s cybersecurity defenses. Firewall management is crucial for keeping a secure network and lowering the risks from online threats. Additionally, IPAM offers firewall management, which functions similarly.
What exactly is firewall management?
A particular firewall is specially set and managed through the process of firewall management in order to ensure a secure network. Both household and commercial network security rely heavily on firewalls.
A business may by default employ a variety of firewalls to safeguard its devices and network. These firewalls must be managed, which includes establishing guidelines and standards, monitoring modifications, and keeping an eye on compliance logs. Another part of it involves tracking user access to firewall settings. The configuration ensures the firewall’s secure and effective operation.
Any size business with a private network will employ a firewall to protect its systems. This might be a huge contractor that needs to achieve Cybersecurity Maturity Model Certification or a small office network (CMMC). Firewalls play a vital part in IT security rules since they are essential to cybersecurity. In the end, firewall management falls under the purview of whoever is in charge of the organization’s IT security or compliance initiatives.
Three different kinds of firewalls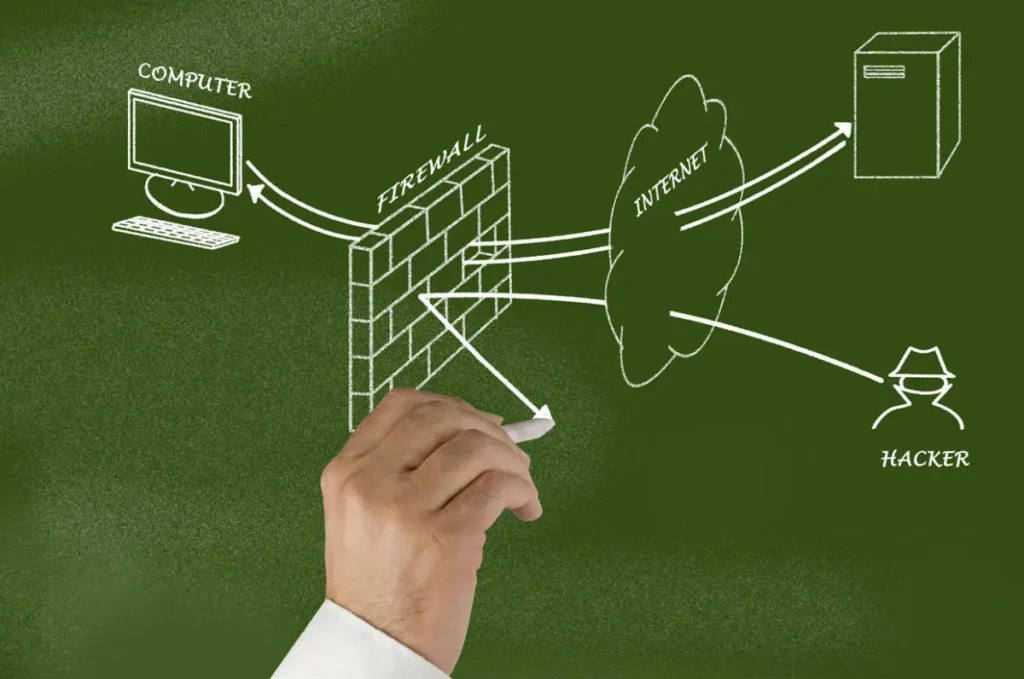
1. Proxies and firewalls
A proxy firewall prevents direct connections between a device and a network by acting as a form of “go-between.” After establishing a connection with a device, the proxy will create the appropriate connections to the network destination. Direct connections are prohibited by a firewall, one of the safest types.
This form of firewall can function on a proxy server or in the cloud. A proxy server caches frequently requested content and keep records as a result of its function as a request bottleneck.
2. Customary firewalls
Stateful and stateless inspection firewalls are terms that are widely used to describe traditional firewalls. According to predetermined criteria like source, destination, or port address, these firewalls control and filter network traffic. These firewalls will allow only trustworthy traffic to enter and leave a network.
Rules can be established and put into effect for certain traffic flows, and traffic from erratic sources can also be stopped. These firewalls are typically present in solutions and pre-built systems.
3. Future-proof firewalls
As their name implies, next-generation firewalls (NGFW) are more advanced iterations of traditional firewalls. Several next-generation firewalls provide the extra feature of traffic filtering depending on apps. This helps to defend businesses against more skilled attackers. They can act as an anti-virus, limiting the ability of specific malware to enter networks. These systems combine traditional firewalls with an intrusion detection system, which actively checks the network for malicious activity.
Next-generation firewalls may be upgraded to meet new cybersecurity threats as they appear, assisting in the identification and mitigation of fresh risks. Therefore, when put into operation, next-generation firewalls offer businesses excellent levels of security.
Firewall Management Advice
You’ve found the best location to look for firewall management advice. Everything you need to know about operating your firewall will be covered in this professional book, from the fundamentals of installing and configuring your firewall to more complex subjects like security and troubleshooting.
1. Determine Your Firewall’s Purpose
You must first determine the level of security you require before you can select the best firewall for your requirements. If you merely need to safeguard your machine from illegal access, a basic firewall like Windows Defender will do the trick. You should spend more money on a firewall that offers additional features if you also want to safeguard your PC against spyware and other harmful applications.
2. Take Your System’s Needs Into Account
For a firewall to function successfully, it needs to be configured differently for each type. For instance, if you want to use a basic Windows Defender firewall, you must only permit certain kinds of traffic to pass through it. You’ll probably need a complete firewall that can block more types of traffic if your system runs more complex applications or apps.
3. Take into Account Your Hardware
You must choose the hardware you have access to before configuring your firewall. Some firewalls, such as a specific firewall for IPv4 and IPv6, need a specific configuration of computer hardware in order to work effectively. You will need to buy this hardware separately if you don’t already have it.
4. Consider Where Your System Is Located
Firewalls can differ based on where your machine is located. If you live in the United States, for instance, a U.S.-based firewall like Windows Defender might be your best choice. However, a European or Asian-based firewall may be more suitable if you are located in Europe or Asia.
Final Thoughts:
When it comes to firewall management, it’s crucial to keep in mind that prevention is always preferable to cure. You may help keep your network secure from attacks by routinely inspecting your system for vulnerabilities and keeping your firewall updated.







Discussion about this post